Mounting Mulitple Drives at Boot Time using LUKS (dm-crypt)

Mounting more than just the root partition at boot using LUKS/dm-crypt is a little more complicating than setting up just the one. Rather than just placing your UUID of the root partition in the /etc/default/grub file you have to go through several more steps. Follow along as I describe a simple way to get more than one partitions/disks mounted at boot time.
When you might not want mount-encrypted drives at boot.
Having encryption at rest built into a partition/disk is a great way to keep those who have physically compromised said disk out from reading your data easily.
Having said that though, if your system is currently running and that same disk/partition is mounted and unencrypted and someone were able to have access, then you lose all of the benefits of encryption.
If you require sensitive data to be on the disk/partition then you really should be locking and unlocking the encrypted device manually instead.
If security is a concern but you limit aspects of physical access while the system is running then you might want the convenience of unlocking at boot time which is what this post is all about.
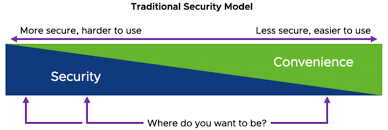
This graph shows the security to convenience ratio.
Setup a partition
This assumes the new HDD or SSD we want to use is /dev/sda. Also be aware this will delete all data on that drive.
Let’s first build a new filesystem on the HDD or SSD on /dev/sda.
$ sudo gdisk /dev/sda
p # print all avaiable partions.
d # delete a partion. We should delete all we don't need. Usually you will want to use the entire disk.
c # create a new partition.
Hit --ENTER--
Hit --ENTER--
Hit --ENTER--
t # changes the partition format.
8300 # for a Linux filesystem
p # show the partions again. Should only be one if we wiped all the other ones.
w # writes to disk
q # quit/exit
If we run sudo fdisk -l we should now see a /dev/sda1 partition available.
Setting up the drive and crypttab
Here we are formatting the drive and setting it up with cryptsetup which is the encryption program used in LUKS.
$ sudo cryptsetup luksFormat /dev/sda
# A warning and confirmation will appear here. Type YES in all uppercase and enter your super strong passphrase twice.
$ sudo cryptsetup luksOpen /dev/sda crypt_storage
# change crypt_storage to whatever you want it to be. This be used later for mapping purposes.
$ sudo mkfs.ext4 /dev/mapper/crypt_storage
# here we will install the ext4 filesystem on the mapped drive as mentioned above. This a linked location as this is easier to remember than a long sting of UUID and or if the HDD changes letters ie., /dev//sdc or /dev/sdx.
Next let’s create a mount point and directory for the newly formatted encrypted drive.
$ sudo mkdir /storage
$ sudo mount /dev/mapper/crypt_storage /storage
At this point the drive is fully usable and will store data but the encryption will only happen when it has been unmounted and or its powered off. Also next time we reboot, the drive will be in the encrypted stage and we will have to run the cryptsetup luksOpen again just to unencrypt it.
Let’s now make to where the drive will be unencrypted and mounted after every reboot.
Adding a key file and automounting
Let’s first build a random keyfile, place it in the root directory, change the permission of it, and finally add the key to cryptsetup.
$ sudo dd if=/dev/urandom of=/root/.data.key bs=1M count=4
$ sudo chmod 0400 /root/.data.key
$ sudo cryptsetup luksAddKey /dev/sda /root/.data.key
Now we can add our UUID of /dev/sda to the /etc/crypttab file.
$ sudo blkid | grep /dev/sda >> /etc/crypttab
$ cat /etc/cypttab
/dev/sda: UUID="xxxx-xxxx-xxxx" TYPE="crypto_LUKS" PARTLABEL="" PARTUUID="xxxx-xxxx-xxxx"
$ sudo vim /etc/crypttab
# add a new line and insert with your UUID and NOT PARTUUID if you have one. Make sure to not use the quotes. The first entry (data) can be be replaced with anything, ie., storage, crypt2, super_secure, etc.
secure_storage UUID=xxxx-xxxx-xxxx /root/.data.key luks
Just like we did above we will want to grab the UUID of /dev/sda and use that as a reference to put into our /etc/fstab config file.
$ sudo blkid /dev/sda >> /etc/fstab
$ sudo vim /etc/fstab
# replace with your UUID below. Make sure to not use the quotes. Also change the directory it will be in ie., /storage or wherever you want. Just make sure the folder exists first.
UUID=xxxx-xxxx-xxxx /storage ext4 defaults 0 0
We can auto mount and test this by running sudo mount -a.
Unmounting
You can also unmount the drive manually if you needed to do so by running:
$ sudo umount /dev/mapper/crypt_storage
$ sudo cryptsetup luksClose /dev/mapper/crypt_storage
This will re-encrypt the drive and unmount it.
Final
Follow the steps above to run the setup across multiple device.